How to Identify If an Email is a Security Risk

There’s one major reason why email is the preferred method of spreading threats like ransomware and other types of malicious software. The sheer number of messages that can be sent through email on its own increases the odds that a user will click on the wrong link or download the wrong attachment. How can you know the legitimacy of any message you receive in your email inbox?
How to Identify If an Email is a Security Risk

There’s one major reason why email is the preferred method of spreading threats like ransomware and other types of malicious software. The sheer number of messages that can be sent through email on its own increases the odds that a user will click on the wrong link or download the wrong attachment. How can you know the legitimacy of any message you receive in your email inbox?
How to Identify If an Email is a Security Risk

There’s one major reason why email is the preferred method of spreading threats like ransomware and other types of malicious software. The sheer number of messages that can be sent through email on its own increases the odds that a user will click on the wrong link or download the wrong attachment. How can you know the legitimacy of any message you receive in your email inbox?
It all starts by being aware of the issue at hand and staying vigilant of any potential threats. You should actively look for reasons not to click on links in suspicious emails. You can never be too careful, especially when there is so much on the line. Here are three warning signs that you can look for to avoid a malware attack via email.
Spelling and Grammar Errors
Nobody has perfect spelling and grammar, and it’s forgivable if they make a mistake here or there, but when an email is filled with errors that make it hard to believe its authenticity, perhaps you’re staring a red flag in the face. Professional messages will at least contain passable grammar that makes them easy to understand, but a malicious message might be filled with all sorts of nonsense that urges you to click on a link or download an attachment. Sometimes you might encounter a phishing email that’s very discreet, but this is more of an exception than the norm.
Links Leading to Suspicious or Unfamiliar Targets
Let’s say that you receive a message from your bank. When you hover over a link in the message, it shows that the link doesn’t lead to any site you’re familiar with. This is a clear indicator that you might be looking at a very well-orchestrated phishing scam. Before clicking on any link, just hover your cursor over it without clicking on it. In a bar at the bottom of your browser, you’ll see the target of the link. If it looks suspicious, you can easily disregard it or report it to IT.
Messages from Unknown Senders
Who did you receive the message from? If you know who sent the message, then perhaps the message is legitimate. However, it’s easy for hackers to spoof an email address and make it appear that someone else is sending a message. Remember, suspicion is better than falling into a trap. In a worst-case scenario, even a CEO or upper-level employee could have their account spoofed in a phishing or whaling scheme. If you suspect that this has happened, notify your IT department immediately so that measures can be taken against these efforts.
Thankfully, with a little bit of thought and caution, you can avoid most fraudulent emails, but it would be nicer if you didn’t have to worry about seeing these messages in the first place. An enterprise-level spam filter can keep fraudulent and spam messages at bay. To learn more, reach out to us at (317) 705-0333.
Email Malware is the New Schrӧdinger’s Cat
There is a famous thought experiment devised by physicist Erwin Schrӧdinger, describing a very particular paradox in quantum physics through the experience of a cat. While Schrӧdinger’s cat was initially intended to demonstrate a very different phenomenon, it can also be applied to something that all businesses need to consider: their email security.
Schrӧdinger devised the thought experiment to combat the Copenhagen interpretation of quantum mechanics, which posited that, when unobserved, an object can exist in all states, and reverts to one if observed. In Schrӧdinger’s thought experiment, a cat was hypothetically shut in a box with a small enough amount of radioactive material to only have a 50/50 chance of being detected by a Geiger counter. If it was, a hammer would break open a container of poison, killing the cat. The premise was that, if the Copenhagen interpretation was correct, the cat could be assumed to be both alive and dead simultaneously until it was observed to be one or the other.
While Schrӧdinger’s cat was meant to discredit the Copenhagen interpretation, there is a modern version of this thought experiment that businesses should be concerned about. This version focuses on email, and the attachments that often come with it.
It is no secret that email is a very popular way for cybercriminals and other online mischief-makers to deliver their tools. If we treat emails the way that Schrodinger’s cat was approached, any email could feasibly contain a malicious threat, as well as no threats at all. The thing is, while determining if Schrӧdinger’s cat was alive or dead would be a relatively harmless activity (except potentially for the cat), finding out whether or not an email attachment is infected could cause quite a bit of damage to your system.
Fortunately, there are ways to protect yourself and your system against threats like email malware and phishing attempts. Antivirus and anti-malware scanners can catch many threats on their way in, and a spam blocker can help keep out many more.
If you’d rather know for sure that your inbox doesn’t contain any threats (or dead cats), let Catalyst Technology Group suggest a few solutions. Give us a call at (317) 705-0333.
Have You Implemented Email Encryption?

If you don’t take measures to secure your email, you could potentially give up crucial information to anyone lurking on the same network as you. This is inevitable on public Wi-Fi connections, or anywhere data is in transit. Encryption is the best way to make sure that your organization’s communications are secure, so you absolutely want to encrypt your email.
Why Does It Matter?
Encryption matters for the express purpose of keeping your communications as private as possible. Your email provider may or may not offer encryption by default, but there’s never a good reason to expose your business’ data to dangerous entities. While you’re putting your business’ data at risk, you could also be putting your business itself at risk due to data privacy regulations.
Long story short, encryption is critical if your organization wants to avoid the dangerous part of the Internet. This includes hackers, who will go to great lengths to steal your business’ data, despite the protections that your company puts into place. Therefore, it’s incredibly important that your company put these measures into place so as to improve the chances that you are able to keep your business secure.
How Does Encryption Work?
To explain encryption, we’ll use the locked box analogy. Imagine that you have a box containing your emails that can only be unlocked by someone with a special key. Whoever you send the box to has the key, and it will be unlocked upon receipt. Even if the box has been intercepted, it can’t be opened without the right key, meaning that the thief won’t have any use for it.
The most important part of encryption implementation is that it needs to be applied to your entire infrastructure. If you only encrypt messages that contain sensitive information, you’re only making yourself a larger target. If you do choose to implement an encryption system, it should be associated with more than just your email security.
Catalyst Technology Group can help your business implement a quality email encryption solution designed to augment your security and privacy. To learn more, reach out to us at (317) 705-0333.
Scam Leverages Email from a Reluctant Contract Killer

To many, email scams have become a joke. Sitcoms have throwaway punchlines that reference a character getting an email from a rich uncle in Nigeria, or some friend needing funds to get home from an overseas trip. One of these scams may not at first seem to be amusing, as it threatens the recipient’s life, but if read further, proves to be quite the drama.
Upon accessing their inbox to find an email with the subject: “Please read this it can be the most important information in your life,” the target opens the message to discover that there has been an evil plot taking shape to do them in. While this email is completely a scam, it is entertaining enough to review here, if only to show how creative cybercriminals can be.
The email itself informs the recipient that the sender, a professional hitman, has been hired to execute them. According to the email, this order was passed to the contract killer because the recipient’s “activity causes trouble to a particular person.” However, after studying the target, the hitman has had a change of heart and is therefore offering the target a chance to save themselves–something that will blackball the hitman and ruin the reputation built on twelve years of successful contracts.
The recipient then learns that the hitman was looking to get out of the game anyway, and so this offers a mutually beneficial solution. For 0.5 Bitcoin (worth well over $ 5000), instead of carrying out the kill, the assassin will instead turn over the name of the person who hired them, along with incriminating evidence to bring to the police. Of course, the hitman warns, the target should not go immediately to the police, as their investigation would take longer than the two days the target has to accept the arrangement.
Finally, the hitman promises to make contact again once the funds have been transferred, and apologizes for their career, stating:
“I really regret that you became my prey.”
Despite (or perhaps due to) the letter reading like the synopsis of a summertime Hollywood blockbuster, the scammer responsible has yet to collect any funds in the online wallet they provide in their letter. Of course, this may also be in part because of the demand of the 0.5 Bitcoin, which isn’t exactly pocket change.
Now that you know this, don’t be the first to hand over a few thousand dollars for an empty threat. Instead, if you happen to receive one of these emails, mark it as spam. This will help teach the spam filters that this is an unwanted email, and might help to keep it from reaching someone else’s inbox.
For more information to help you dodge the scams that cybercriminals leverage, give Catalyst Technology Group a call at (317) 705-0333.
Looking at the Landscape of Email Fraud

Email is arguably the most popular method of business correspondence in existence. It’s fast, economical, securable, easy to store/archive, and searchable in a way that traditional, physical records can’t compete with. With billions of emails sent every day from all over the globe, there is a considerable amount of sensitive information transmitted within these communications. The criminal element is looking for every opportunity to steal and exploit personal data, as well as take advantage of vulnerabilities to gain access to a company’s data or network.
One particularly effective method of email fraud is impersonation. Sometimes falling under the categories of phishing, whaling, or SMiShing, impersonation email emulates a legitimate address from a non-threatening source that convinces the user to take an action. An example of an impersonating email fraud would be a user transferring funds to a 3rd party account on the order of what they believe is a legitimate message from their CEO, but actually originates from a spoofed email address. Another example would be if someone opened an email attachment that appeared to be a legitimate spreadsheet but actually introduces ransomware into their network.
Email Security by the Numbers
For those who are looking to visualize the risks associated with email fraud, here’s a look at a few recent statistics that show just how big of a problem it can be for a business.
- In 2017, the number of worldwide email users will top 3.7 billion, or about half of the worldwide population uses email in 2017.
- Phishing attacks make up about 91% of all attempted cyberattacks.
- Top three reasons people are duped by phishing emails are curiosity (13.7%), fear (13.4%), and urgency (13.2%).
- Email fraud was the 2nd most frequent successful external intrusion method in 2017.
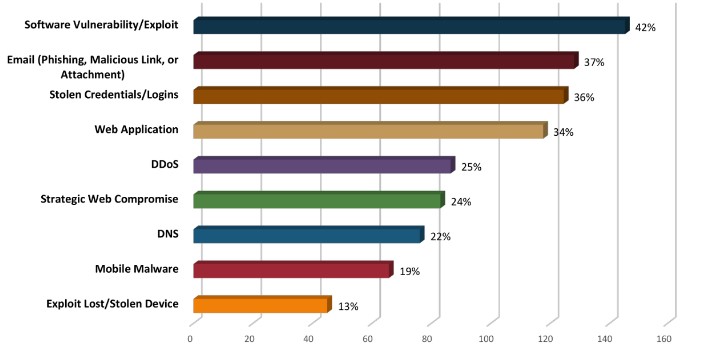
- 0.5% of the top million domains are protected from impersonation by email authentication.
- Implementing email authentication would save the average company $ 8.1 million per year in cybercrime costs—$ 16.2 billion annually across the Fortune 2000.
- Business Email Compromise (BEC), also known as CEO impersonation, losses are up 1,300%
Reducing your Business’ Risk of Email Fraud
Most email security experts agree that implementing two encryption and authentication standards are the first steps to reducing the number of cyber security gaps that have been proven to increase risk of email fraud.
- DMARC: The first standard, Domain-based Message Authentication, Reporting, and Conformance, or DMARC, authenticates an email domain, ensuring that the sender’s information aligns with the known information about the authenticated domain. DMARC has been found to detect the majority of email spoofing and impersonation and handle them according to the receiver’s procedure – usually by flagging them as spam.
- STARTTLS: The second standard, called STARTTLS, is a command that orders a secured connection that subsequently encrypts the email data being sent and received.
DMARC and STARTTLS standards have proved so effective at email fraud prevention that, on October 16, 2017, the U.S. Department of Homeland Security ordered ALL federal agencies to implement both of them within 90 days.
Federally Mandated Email Regulations for Businesses
DHS isn’t the only organization requiring email encryption as part of their technology regulations and compliances.
- HIPAA: Those entities in the healthcare industry that are required to be in compliance with the Health Insurance Portability and Accountability Act (HIPAA) must implement access controls, audit controls, integrity controls, ID authentication, and transmission security before an email correspondence that includes personal health information is considered to be “in compliance”.
- PCI-DSS: Companies that use customer credit card information are required to meet PCI data security standard. The PCI-DSS expressly advises organizations to never use email, encrypted or otherwise, to share credit card data. Because emails are generally stored for long periods of time, it violates the PCI rules regarding card information storage after authorization and maintenance of access control at all times. Still, many PCI compliant businesses choose to use email encryption as an additional security measure.
Catalyst Technology Group Has Your Back!
For most small businesses, the idea of tackling any type of email fraud prevention on their own is extremely overwhelming. It’s a world of protocols and acronyms that the average IT decision maker often prefers to avoid altogether – and that’s just encryption. To get the maximum productivity while maintaining network and data security, modern businesses should leverage spam filters, antivirus and malware scanning, archiving/storage, hosting considerations, acceptable use policies, access control, and more. In the end, an email solution can have a large impact on a company’s daily operations.
The good news is that you don’t have to fight cybercriminals alone! Catalyst Technology Group is well acquainted with all types of cybersecurity – including email authentication and encryption. Our experts will help you find the perfect email fraud protection strategy to meet the needs of your business. Contact us at (317) 705-0333 and get encrypted.
Why Your In-House Email Server Probably Isn’t Worth The Trouble

Most businesses rely on email in at least some capacity. Nowadays, organizations often choose to outsource the management of their email servers, including their hosting, to other organizations, most notably cloud providers for ease of use. Here are some of the benefits that you can gain from switching your in-house email management to a cloud-based email server.
It’s Less Expensive
If we asked you how old your exchange server is, would you be able to fit the number of years on one hand? There is a fair-enough chance that it’s an older piece of hardware, which means that it inevitably costs more to run and maintain. Older technology tends to break down more often, and it can quickly become an asset sink in the long run. Not only is it an expensive approach to email management, but it’s also an outdated practice. Why host your email server in-house when you have so many great cloud providers like Microsoft and Google that can accomplish the same task in a better way?
Control Is a Non-Issue
Having an in-house server comes with more control, but this is something that is constantly changing. Cloud-hosted solutions often come with many customization options. Additionally, you’re protected against the problems that could arise from having a physical server unit. Think about a power outage or a fire, for example. A cloud-based email server can continue running even when the conditions for an in-house server unit aren’t ideal.
A cloud email solution also comes with various protections against online threats, like viruses and malware. Since email is such an important part of any business venture, it must be isolated from other parts of your infrastructure so as not to jeopardize your network.
Less On-Premise Infrastructure
Your employees need constant access to data, including email. While each system is responsible for one particular goal, progress can come undone if even one of these systems fails to function properly. If your email server encounters trouble, it needs to be fixed, as communications could be halted. This could lead to miscommunications and work not being done properly, causing tasks to be repeated and time being wasted. Thanks to the cloud eliminating many of the components found in the traditional in-house infrastructure, you’ll be able to keep it as simple as possible. You won’t miss maintaining multiple hardware solutions on a day-to-day basis.
Does your business need a hand with email server management? To learn more, reach out to Catalyst Technology Group at (317) 705-0333.

