Chromebooks Deserve More Credit than You Might Think

It can be easy to dismiss the simple Chromebook as a limited solution, a one-trick pony of technology. However, while this may have once been true of the devices, more recent models are capable of much more than their predecessors. We’ll address a few misconceptions people have about, and against, Chromebooks.
Is Your Printer Wasting More Money Than it’s Worth?

Is your printer printing dollars, or eating them? Today’s blog is dedicated toward helping your business save as much money as possible on printing costs so that you can achieve the best return on your printing investment.
Is Your Printer Wasting More Money Than it’s Worth?

Is your printer printing dollars, or eating them? Today’s blog is dedicated toward helping your business save as much money as possible on printing costs so that you can achieve the best return on your printing investment.
More Victims of the Equifax Breach Discovered

The 2017 Equifax leak was a disastrous scenario, but recent revelations have discovered that even more victims were affected than was previously thought. Nobody ever wants to hear this kind of news, but there is an upside to this that shouldn’t be ignored – learning from the mistake. We’ll start with a refresher on what happened exactly, and what these new developments mean for your organization.
The Breach of 2017
Equifax is one of the three major credit reporting organizations, and it suffered a major data breach in 2017. Over 143 million users were affected by this breach and potentially had their personal information stolen or provided to hackers. For those who are curious, this is about 44 percent of the United States total population. It’s pretty wild to think about. In October 2017, an investigation yielded more information that showed about 2.5 million more users were exposed than the original numbers let on. Thus, the total number of victims reached a staggering 145.5 million, or nearly one half of the entire U.S. population. If anything, this new development showcases that this number is not set in stone and that it could potentially increase over time.
For example, Equifax has discovered even more victims; 2.4 million more who have had their names and partial driver’s license numbers stolen. Unlike other information that holds greater value, a hacker can only do so much with this data, but it’s still problematic.
Lessons from the Breach
One of the most important lessons that you can learn from a data breach is that there is always going to be another data breach. Businesses just hold onto too much valuable data, and too many people are looking to steal it, for there to be any other outcome. The fact that so much information is shared and distributed all over just makes it more likely that information will be breached. Therefore, measures must be taken to ensure that your company doesn’t suffer the same fate as Equifax.
You have to understand that your data will be potentially stolen or exposed, and not because of you. It could be the fault of any company that holds your information. Just like Equifax, any companies that work with your data could potentially lose track of, and expose it, too dangerous entities. Even if you do nothing wrong, it could happen. You need to take measures to both protect yourself and prevent attempts at identity theft due to the negligence of others. You can start with credit freezes, locks, and alerts.
The next step is to be careful of who specifically you share this information with. If you share information and it’s compromised in any way, you could find yourself at odds with your clients and customers. Therefore, it makes sense that you take measures to limit this risk as much as possible.
Don’t let a data breach that your business suffers from be the reason why your organization implements security. Call us today at (317) 705-0333 to get started.
Digital Signatures are More Efficient and Secure

Your signature has a lot of power, particularly in the business world. Because of this, it’s curious to see how so many companies are moving over to the more digital alternative. In order to fully take advantage of digital signatures for your organization, you need comprehensive security measures that can reinforce the authenticity of your signatures.
This movement to digital signature software is further augmented by electronic document storage. Hoping to reduce the amount of paper waste and printing costs, businesses have started to keep digital documents rather than physical file storage, which naturally makes digital signature software much more valuable as a whole. Going paperless allows organizations to ditch the bulky filing cabinets and allow for easy file searching.
Until digital signature took off, users would have to electronically “sign” documents by printing them out, signing them, and then either scanning them or mailing them to where they needed to go. Thanks to PDF editing software, it’s easier to move in the direction of digital signatures than ever before.
Understanding Digital Signatures
Official documents require a signature, which means that there will always be value for digital signing software. Digital signing solutions allow companies to sign documents even while working remotely, which creates more opportunity and provides more convenience as a whole. You can forget the original methodology of scanning, sending, printing, and so on. Forging signatures is much more tempting when getting the official signature is difficult, which can potentially help you dodge a worst-case scenario.
PDF software allows your organization to know for certain that a digital signature is more than just a scribble on a piece of paper. It has its roots in cryptography, which is a technology that is used by most secure transactions out there. It essentially works like this; a digital signature has digital keys attached to it that can confirm the identity of whoever signs it. Since digital signature uses encryption, it’s easier to know that your signatures are as authentic as possible.
Just like with a physical signature, you’ll see a graphical representation of the signature, a name of your choosing, and the location of where the document was signed. Furthermore, you’ll also receive a timestamp that shows when the signature was filed. Keep in mind that each solution is different, however. Not all PDF software solutions are the same. Investing in one is a great benefit, however, as you can move in the direction of flexibility for your organization.
For more information about digital signatures, reach out to Catalyst Technology Group at (317) 705-0333.
Which is More Secure, Your Mobile Network or Wi-Fi?

For the modern business, having a strategy to manage your employees smartphone use is essential. This is because most of the people that work for you have smartphones. One study shows that upwards of 90 percent of people under 30 own a smartphone. If you have any design on running a business, or employing millennials (who are the largest generation in the current workforce), you’ll need to know what you are doing to protect your business from the increasing amount of threats that are out there targeting smartphones.
An annual Wi-Fi Security Report conducted by Wandera found that, out of a sample of 100,000 corporate-owned mobile devices, 74% of wireless data was transferred using a Wi-Fi network, 12 percent of Wi-Fi hotspots used by those people are open and lacking encryption, and only four percent of these corporate-owned devices have been exposed to malware through an accidental or deliberate man-in-the-middle attack.
The man-in-the-middle attack (MiTM) is one where a computer will pick up malware that allows an intermediary to intercept files and correspondence between the two machines, and upon connecting to a network via a Wi-Fi connection, transfers the malware onto the computing network–thus infecting the network with the malware that allows the hacker to intercept any communication.
It’s largely understood that cellular networks are more secure than Wi-Fi networks, as cellular networks utilize high-end encryption techniques. This doesn’t make them popular, however. People will typically use Wi-Fi that is available. In fact, one statistic suggests that people are so addicted to the use of Wi-Fi that upwards of 60 percent of people will connect to any available public Wi-Fi rather than use the cellular data, even if they don’t pay for it themselves. Symantec’s Wi-Fi Risk Report corroborates this notion, adding that roughly the same number of people believe their personal information is more secure transmitted over Wi-Fi, and that 53 percent cannot tell the difference between a secure and unsecure Wi-Fi network. The report goes on to state that nearly nine out of ten consumers have put their information at risk by using public Wi-Fi.
At the business level things get a little better. While individual Wi-Fi use remains similar, businesses typically do a much better job of securing their network to keep malicious entities out. One way they do this is by setting up a firewall to keep their Wi-Fi networks away from the rest of their network. Typically, when a person accesses your organization’s Wi-Fi, they are then able to access your whole entire network. If your servers and other confidential data are linked to your organizational Wi-Fi, then an intruder who can manage to connect will then have access. By separating your Wi-Fi from your network behind a firewall, you will not only protect yourself from ambitiously malignant people on your network, but also go a long way toward safeguarding your network from cyber attacks in general.
Another way that the business can ensure their mobile strategy won’t hamstring their company’s network is by instituting a Virtual Private Network (VPN). The VPN brings additional encryption to data communication by creating a secure tunnel in which to transfer data. For the small business a VPN has become an almost essential part of providing your staff with a workable remote computing situation. Not only does it work to secure your business’ data while using available remote connections, it makes it easier to scale a business by allowing new systems to connect to it with minimal configuration. In doing so, the deployment of a strategic VPN reduces capital investment and is a major benefit for organizational mobility.
If you haven’t already, your business is going to have to address your mobile security before it gets burned. If you would like to learn more about what you are up against, or how you can utilize today’s security technology to protect your business’ important data, call Catalyst Technology Group today at (317) 705-0333.
Tip of the Week: Cortana Can Do Even More than You Might Realize
One of the most recognizable names in technology isn’t a person, it’s a virtual assistant: Cortana. While Cortana has been of great use to many users, sometimes that user isn’t actually the person who owns the device and is just someone else in the same room. This can be annoying, but there’s a way to acquaint Cortana with a single user’s voice and listen to them exclusively.
To set this up, you’ll need to access Cortana’s Settings. First, click on the Cortana Icon that appears on the taskbar.

Next, access the settings menu for Cortana by clicking on the gear icon in the Cortana window that appears.
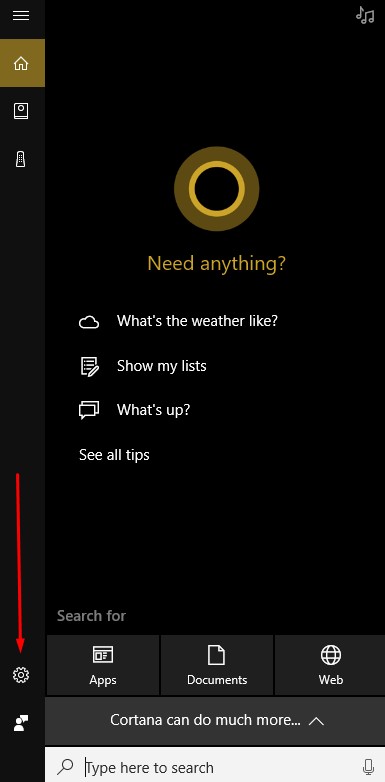
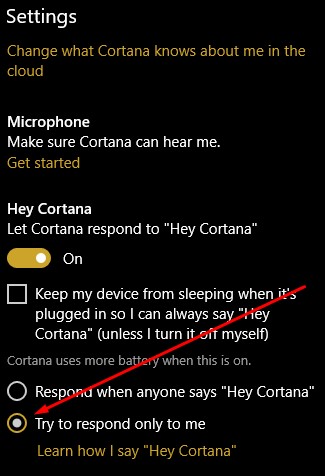
Activate Let Cortana respond to “Hey Cortana” and select Learn how I say “Hey Cortana.”
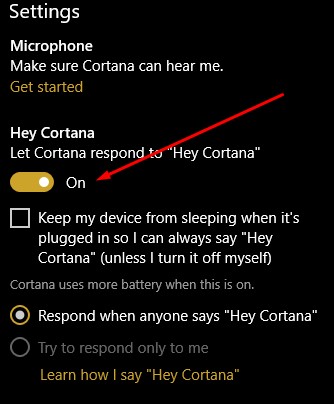
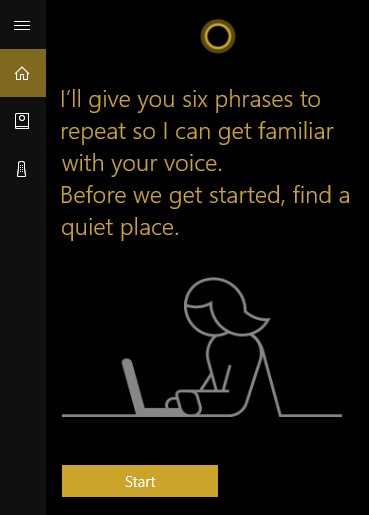
Once you do so, you will be prompted to recite six phrases so that Cortana can establish how you will say “Hey Cortana.”
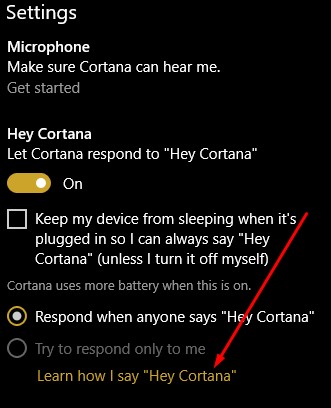
After this exercise is completed, go back to Cortana’s settings and confirm that try to respond only to me is selected.
Cortana is now primed to listen to only you and you can now use it for many purposes, including to navigate Windows 10.
Are there any other assistants you use, like Alexa, the Google Assistant, Siri, or Bixby? Which one is your favorite? Tell us why in the comments section!
Facebook, Gmail, and Slack are Becoming More Collaborative

In the modern business setting, collaboration drives productivity. As a result, many software developers are producing software with collaboration in mind. Since these developers are all in competition with each other for market share, they are typically trying to build on more advanced features to outmaneuver the other companies. Some of the biggest names in the industry have recently updated their products to make collaboration a priority. This week we’ll take a look at updates made to Facebook Workplace, Gmail, and Slack.
Facebook Workplace
Communication drives collaboration. Facebook has rolled out a new desktop app to work with the chat element within their productivity network app, Workplace. Called Workplace Chat, the application allows users to easily swap files and share screens for more dynamic collaborative processes. Down the road, Workplace Chat will support third-party applications to improve collaborative function for the thousands of companies that utilize the Facebook Workplace platform.
Apps for Gmail
Google’s strategy is to improve Gmail’s utility in the collaboration-minded setting of the modern business. They have begun to look to third-party developers to find collaborative solutions. Companies like RingCentral, Trello, DocuSign, Intuit and more have working integrations with Gmail, making the email provider better suited for the collaborative business than ever before. With the millions of users that utilize Gmail, and the flexibility Google is offering app developers, it’s no surprise to find out that new companies are actively creating software for the platform.
Slack Adds Improved Screen Sharing
One way to improve collaboration is with the addition of screen-sharing functionality. Slack was designed to promote collaboration in the first place, and has improved it’s screen sharing function to include interactivity. The Slack platform is intended to create employee alignment and a shared understanding of a project; and, with screen sharing capabilities updated for paid subscribers, teams that use the application will benefit from this additional functionality. Users will be able to create temporary notes, navigate through documents better, and edit documents freely, giving the whole interface a substantial upgrade.
What does your organization do to help improve collaboration? If you have a useful application that could be of help to another reader, please don’t hesitate to post it in our comments section below.
Android Starts Zero-Touch With Google Pixel, More To Follow?

Google’s Android line of smart devices have made their presence well-known in the business world. Google now offers a zero-touch enterprise solution for its Pixel-line mobile devices. The primary reason for this is that mobile devices are somewhat time-consuming to set up, especially on the business level. You can save time by pre-configuring these devices for your business to use using Pixel’s zero-touch solution.
This isn’t the first time that Google has targeted businesses with their line of smart devices. With special editions of the Google Play store, additional security solutions, and management dashboards, businesses can customize their devices as they see fit. However, since all businesses are different, the amount of time it takes to configure each and every device for various departments can vary significantly between organizations. This is why it’s so beneficial to get these devices almost completely pre-configured.
This type of device management might sound ideal, but it has a couple of limitations that are worth mentioning. Zero-Touch is only available through carrier opt-in (in this case Verizon) in the United States, and it’s only possible on the Google Pixel line of smartphones. Other providers, including AT&T, Sprint, and T-Mobile also plan on implementing zero-touch at a later date.
Furthermore, third-party Android device manufacturers also want a stake in this development. Manufacturers like Samsung, HTC, Huawei, Sony, LG, Blackberry, and Motorola all want to help bring zero-touch to more businesses.
This type of solution solves one of the most challenging parts of implementing mobile devices in the business world: multiple devices using different operating systems. If there’s no uniform standards for your mobile devices, maintenance becomes more difficult. This is called fragmentation, and it’s something that has been happening ever since different mobile OSes were introduced.
Does your business need a way to better handle mobile devices? If so, reach out to Catalyst Technology Group at (317) 705-0333.
Data Backup is Much More Complicated Than It Seems

You must consider a series of worst-case scenarios if you want to protect your business in the long run. While various factors such as physical security, employee training, and network security can help you mitigate the majority of issues you face, what happens when each of these efforts fails? You know what they say–prepare for the worst and you’ll never be surprised by a data loss event again.
With a quality data backup and disaster recovery solution, you’ll be prepared for whatever life throws at your business. Larger companies generally don’t have as much to worry about, as their budgets are more flexible and can accommodate the spending required to ensure business continuity. Yet, smaller businesses can take advantage of these benefits as well, and it’s all thanks to managed IT services. The same backup and disaster recovery services that large enterprises take advantage of can work for your business, too, and it all starts with a business continuity plan. Here are four major concerns that any SMB should take into consideration for preserving their data infrastructure.
Firewalls
Do you store your business’s data backups in a location where they’re not protected by security solutions? If so, you’ll need to reconsider how you store your data backups. Firewalls are designed to keep threats from traveling to and from your infrastructure, and if the data that you’re storing your data backups in isn’t adequately protected by them, you’re going to have a bad time.
Antivirus
The same can be said for an antivirus solution, which protects your data by eliminating threats to it. All it takes is one threat to corrupt your business’s computing infrastructure. Think about what would happen if your data backups were to be corrupted by some ransom strain of malware. Would you be able to restore a backup like that in good faith that it wouldn’t pose a threat to your organization? Probably not–and you shouldn’t be in this situation in the first place. Implement an enterprise-level antivirus solution so that you don’t have to worry about whether your data backups are any good.
Backup Tests
Let’s say that your business experiences a data loss incident. You try to restore your data as soon as possible, but something goes wrong. The data is corrupted. It’s not as complete as you’d like it to be. Regardless of the reason, your business is down and out because you just assumed that your data backups would work as intended. You should be periodically testing your data backups to ensure that they will work when called upon.
Use Automation
The chances of your business’s data backups not working as intended will be drastically reduced if you remove one of the most unpredictable parts of it–the human element. Tape backups require your employees setting tapes to run backups at the end of every day. A cloud-based BDR, however, will accomplish the same goal automatically and send the backup directly to the cloud. There is no room for error here. Everything is handled seamlessly and without human intervention.
Does your business have a comprehensive business continuity plan? If not, be sure to give us a call at (317) 705-0333. Our trusted technicians can help you build the perfect backup solution for your business.

