Chromebooks Deserve More Credit than You Might Think

It can be easy to dismiss the simple Chromebook as a limited solution, a one-trick pony of technology. However, while this may have once been true of the devices, more recent models are capable of much more than their predecessors. We’ll address a few misconceptions people have about, and against, Chromebooks.
Is Your Printer Wasting More Money Than it’s Worth?

Is your printer printing dollars, or eating them? Today’s blog is dedicated toward helping your business save as much money as possible on printing costs so that you can achieve the best return on your printing investment.
Is Your Printer Wasting More Money Than it’s Worth?

Is your printer printing dollars, or eating them? Today’s blog is dedicated toward helping your business save as much money as possible on printing costs so that you can achieve the best return on your printing investment.
When it Comes to Security, Two Factors are Better Than One

The password isn’t nearly as secure as it used to be. Hackers have begun to take advantage of extremely powerful solutions designed to brute force their way into accounts by using software to rapidly guess thousands of passwords per second, making it extraordinarily difficult to prepare yourself for them. What’s the best way to guarantee that passwords aren’t going to be the downfall of your company? A great start is by taking a close look at password best practices and two-factor authentication.
To get started, let’s review the best practices for creating a password. These include the following:
- Use complex passwords: Your passwords should always be a complex string of letters, numbers, and symbols, including both capital and lower-case letters. Try to keep them as random as possible, without including any specific words or phrases if you can help it. This reduces the chance that your password will be guessed by a hacker.
- Use different passwords for each account: If you use the same password for every single account you have, you run the risk of one password exposing multiple accounts to hackers. Using multiple complex passwords can make them difficult to remember, however, which leads us into our next point.
- Use a password manager: If you’re following password best practices, you’ll notice that remembering passwords is difficult–especially when they are all different and complex. A password manager can store your passwords in a secure vault for access when they are needed, allowing you to use complex passwords at all times without needing to remember them. It sure beats writing down passwords in a Word document or elsewhere, and it’s much more secure than doing so. There are even password managers for businesses that let employers dish out certain credentials to staff in a safe, secure way.
While password best practices are important to ensure maximum security for your accounts, they’re often not enough to secure your business. Hackers are always trying to find new ways to crack even the most powerful of passwords. This is where two-factor authentication comes in. A hacker might be able to replicate the password, but can they replicate your accounts needed for access?
Two-factor authentication works by using a device or email account as a secondary credential for accessing an account or network. The obvious example is a smartphone, which can receive an SMS text message with a code needed to log into an account. Others might have codes sent to secondary email accounts. Either way, the point is that these types of credentials can only be received by the holders of the device, which is much more difficult for a hacker to take advantage of. There are even some types of two-factor authentication that utilize biometrics and near field communication technology (NFC), allowing for even more complexities that hackers will sigh and shake their heads at.
If your business needs to protect sensitive data, two-factor authentication is definitely one line of defense you will need. Catalyst Technology Group has a solution for you. To learn more, reach out to us at (317) 705-0333.
Tip of the Week: Cortana Can Do Even More than You Might Realize
One of the most recognizable names in technology isn’t a person, it’s a virtual assistant: Cortana. While Cortana has been of great use to many users, sometimes that user isn’t actually the person who owns the device and is just someone else in the same room. This can be annoying, but there’s a way to acquaint Cortana with a single user’s voice and listen to them exclusively.
To set this up, you’ll need to access Cortana’s Settings. First, click on the Cortana Icon that appears on the taskbar.

Next, access the settings menu for Cortana by clicking on the gear icon in the Cortana window that appears.
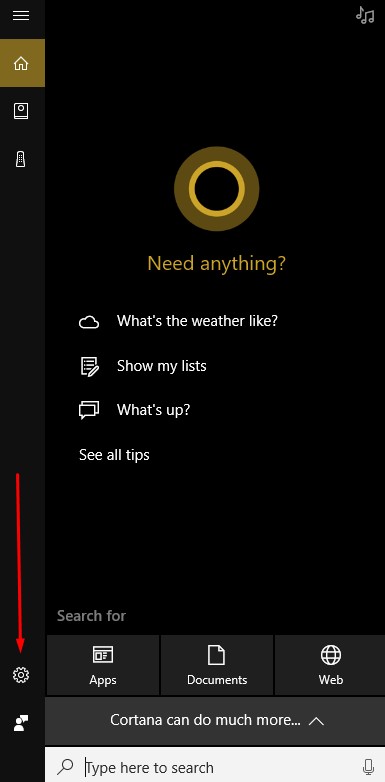
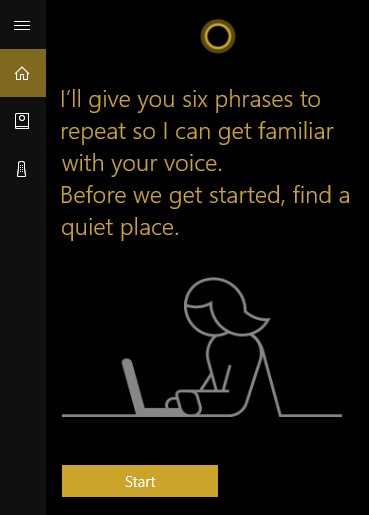
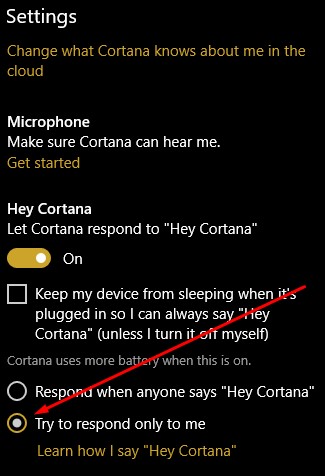
Activate Let Cortana respond to “Hey Cortana” and select Learn how I say “Hey Cortana.”
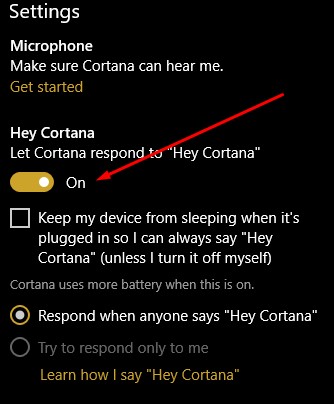
Once you do so, you will be prompted to recite six phrases so that Cortana can establish how you will say “Hey Cortana.”
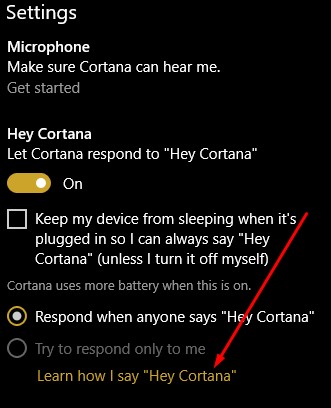
After this exercise is completed, go back to Cortana’s settings and confirm that try to respond only to me is selected.
Cortana is now primed to listen to only you and you can now use it for many purposes, including to navigate Windows 10.
Are there any other assistants you use, like Alexa, the Google Assistant, Siri, or Bixby? Which one is your favorite? Tell us why in the comments section!
Data Backup is Much More Complicated Than It Seems

You must consider a series of worst-case scenarios if you want to protect your business in the long run. While various factors such as physical security, employee training, and network security can help you mitigate the majority of issues you face, what happens when each of these efforts fails? You know what they say–prepare for the worst and you’ll never be surprised by a data loss event again.
With a quality data backup and disaster recovery solution, you’ll be prepared for whatever life throws at your business. Larger companies generally don’t have as much to worry about, as their budgets are more flexible and can accommodate the spending required to ensure business continuity. Yet, smaller businesses can take advantage of these benefits as well, and it’s all thanks to managed IT services. The same backup and disaster recovery services that large enterprises take advantage of can work for your business, too, and it all starts with a business continuity plan. Here are four major concerns that any SMB should take into consideration for preserving their data infrastructure.
Firewalls
Do you store your business’s data backups in a location where they’re not protected by security solutions? If so, you’ll need to reconsider how you store your data backups. Firewalls are designed to keep threats from traveling to and from your infrastructure, and if the data that you’re storing your data backups in isn’t adequately protected by them, you’re going to have a bad time.
Antivirus
The same can be said for an antivirus solution, which protects your data by eliminating threats to it. All it takes is one threat to corrupt your business’s computing infrastructure. Think about what would happen if your data backups were to be corrupted by some ransom strain of malware. Would you be able to restore a backup like that in good faith that it wouldn’t pose a threat to your organization? Probably not–and you shouldn’t be in this situation in the first place. Implement an enterprise-level antivirus solution so that you don’t have to worry about whether your data backups are any good.
Backup Tests
Let’s say that your business experiences a data loss incident. You try to restore your data as soon as possible, but something goes wrong. The data is corrupted. It’s not as complete as you’d like it to be. Regardless of the reason, your business is down and out because you just assumed that your data backups would work as intended. You should be periodically testing your data backups to ensure that they will work when called upon.
Use Automation
The chances of your business’s data backups not working as intended will be drastically reduced if you remove one of the most unpredictable parts of it–the human element. Tape backups require your employees setting tapes to run backups at the end of every day. A cloud-based BDR, however, will accomplish the same goal automatically and send the backup directly to the cloud. There is no room for error here. Everything is handled seamlessly and without human intervention.
Does your business have a comprehensive business continuity plan? If not, be sure to give us a call at (317) 705-0333. Our trusted technicians can help you build the perfect backup solution for your business.
Lowlife Ransomware Hackers Now Asking for More Than $1k Per Attack
Ransomware remains a very real threat, and is arguably only getting worse. Attacks are now able to come more frequently, and there are opportunities for even relative amateurs to level an attack against some unfortunate victim. However, this is not to say that there is nothing you can do to keep your business from becoming another cautionary tale.
Ransomware, in review:
First of all, it’s important to understand exactly what ransomware is. A form of malware, ransomware will infect your system and encrypt your data. It gets its name from the fact that the attacker will demand a ransom in order for your data to be decrypted. What’s worse, if you pay, you’re taking the distributor at their word that they will decrypt your data once the money has changed hands.
Understandably, this form of ransomware can be a highly potent weapon against many users, who simply won’t know how to handle the situation beyond paying and hoping for the best. Of course, since the motives behind ransomware are financial, a lot is directed towards business targets, as they not only have more funds available but are also heavily reliant on their data to function.
Ransomware repercussions
The nature of ransomware means that those that distribute it can usually name their price for the decryption key. After all, it isn’t as though victims have anywhere else to turn other than the hacker (or so the hackers want them to believe). Due to this, ransoms for encrypted data have shot up–in 2015, the ransom to decrypt an infected computer would cost about $ 294, on average. That price had jumped to average $ 1,077 per computer in 2016.
In addition to this increase in ransom demands, there was a 36 percent higher rate of ransomware attempts between 2015 and 2016, 68 percent targeting consumers. This left a still-considerable 32 percent being leveraged towards businesses.
Does it get worse? Sure does.
As if it wasn’t bad enough already, ransomware is now able to be utilized by just about anybody who has a grudge or a desire for some extra cash. Ransomware is now offered as-a-Service, allowing an attack to potentially come from far more sources than before. Some variants of ransomware, such as Karmen, will only cost an aspiring cyber criminal $ 175 to cash in on.
Thankfully, there are steps being taken to eliminate the threat of ransomware. For instance, there are decryption tools to help undo the damage that Karmen can cause because it was derived from the open-source ransomware project Hidden Tear. Other tools and resources are available to help identify which ransomware has infected a given system, like this one from security researcher Michael Gillespie.
However, there are also steps that you can take to avoid a ransomware infection, like following best security practices and computing mindfully. Catalyst Technology Group is here to assist you in putting these procedures in place, as well as helping you recover should ransomware strike. Give us a call at (317) 705-0333 today.

