Tip of the Week: Surfing the Web, Securely

The Internet is often taken for granted, in both a professional and a personal capacity. You’d be hard-pressed to get anything done without it nowadays. This doesn’t mean it’s always safe to do so, however. There are many threats that lurk in the darkness of the Internet, and if you’re not careful, you could find yourself on the receiving end of them. We’ve put together some tips that can help you keep both yourself and your business safe while browsing the web.
Sacrificing Security for the Sake of Convenience
The majority of threats found online can be avoided easily enough–particularly by developing some pro-security habits and practices. That being said, it’s easier to develop bad habits than good ones, as everyone is surely aware of. This only makes it harder to keep yourself safe from online threats.
One great example of this is the password. While it might seem counterintuitive to have more than one password, it becomes a security issue if you use the same password for multiple accounts. This is because a single password is all a criminal would need to hijack multiple online accounts. Therefore, the best way to take advantage of your passwords is to use a unique password for each account, which includes a random string of letters, numbers, and symbols.
If you have trouble remembering passwords, you should never write them down or store them in a document on your computer. Who knows where that file or note will find itself in the future? It’s much safer to simply use a password management system. These allow you to securely save passwords for your accounts in a vault that’s protected by a single master password, eliminating the need for remembering multiple passwords.
Your business can certainly take advantage of a password management system to protect networking components. The last thing you want is to have a hacker access your router and then proceed to the rest of your infrastructure. If you failed to change your router’s initial password, for example, the hacker could easily infiltrate your network and cause all sorts of difficulty for your organization. You can apply the same complex password tips to choosing a password for any device, and augment security by changing the password once in a while.
Additional Strategies
One great way to improve your online security is to always ensure that your tools and programs are up to date. This includes your web browser. Hackers will frequently try to find vulnerabilities within your web browser, even while developers are constantly patching and resolving these issues, leading to a never-ending war towards two very different goals. Who will prevail; the hacker trying to exploit the vulnerability, or the developer seeking to resolve it?
You can make sure that software developers’ efforts aren’t in vain by always implementing the latest patches and updates as soon as they are released. Doing so means that you aren’t needlessly exposing your business’ infrastructure to threats. It also helps to clear your cache once in a while, as well as your browsing history.
Of course, you can be doing much more to improve the way that you browse the Internet. Catalyst Technology Group can provide you with detailed ways to secure your business. To learn more, reach out to us at (317) 705-0333.
Tip of the Week: Comparing the Pros and Cons of Desktops and Laptops

Should your next computer purchase be a desktop or a laptop? Let’s talk about the less obvious differences between the two so you can make the right decision when buying computers for your staff.
Is a Laptop or Desktop the Better Option?
As you might expect, this question more or less hinges on your particular need of mobility. If you find yourself conducting business in various places in (and perhaps occasionally out) of the office, the mobility of a laptop will likely serve you better than a desktop would. Conversely, if your work is more or less contained to the office, a desktop may be more appealing than a laptop. While other factors may also influence your choice, mobility should be one of your primary considerations.
Some other factors to keep in mind are the cost of upkeep of your systems, as well as its intended use. Desktops are often the more cost-effective option, and maintenance is quite often easier. Additionally, a computer capable of more resource-intensive projects–like video editing or CAD rendering, for instance–will cost more, but a laptop will see a faster price increase than a desktop will.
ROI
A desktop can sometimes provide a better return on investment, as they tend to upgrade easier than laptops. This can increase its useful lifetime, allowing your business to remain competitive longer. Another consideration would be reducing your carbon footprint, as you reduce the amount of material going to the landfill.
Checking the Specs
As we just touched on briefly, your intended use of the device should influence your decision considerably. Depending on what you need the computer to be capable of for your business purposes, you may have different requirements than someone else from your organization. For instance, if you primarily use your computer for communications and administrative management, you will not need the same capabilities as someone who regularly uses theirs for advanced, resource-intensive operations. Your role in your organization, as well as the industry you are a member of, will have an impact on this. After all, some industries rely on more data than others, and will therefore have more to manage.
If you’d like assistance in establishing what your particular computing needs are, and which device would serve you best, don’t hesitate to reach out to Catalyst Technology Group for help.
Bargain Hunting
Again, depending on your industry, what qualifies as a good deal for you may be very different than what is considered a good deal for another company that serves a different audience and has different needs. On top of this, there’s also the need to find a reliable vendor who can deliver the technology you need at a reasonable rate – a process that can take an exceptionally long time.
Working with Catalyst Technology Group can help make this process much quicker. You can leverage the relationships we’ve developed with these vendors to get the best deal, while still focusing on your business and leaving negotiations to us.
To discuss your needs and how allowing Catalyst Technology Group to manage your vendors can help fill them, reach out to us at (317) 705-0333.
Tip of the Week: Protecting Your Company from Invoice Impersonation

While you should be sure to keep yourself apprised of threats, it could be argued that it is even more important for your employees to be aware of them. After all, they are the ones utilizing your business’ workstations, software solutions, and even Internet-based apps to facilitate their daily duties. You need to make sure that your employees are able to spot attacks and react to them properly.
While many of today’s employees do have to undergo some sort of security training as part of their employment, the increased sophistication of these attacks makes them more difficult to spot; and, subsequently, harder to react to. One of the most common ways that this occurs is through invoice impersonation attacks. These attacks send customized emails under an assumed name–usually one that is a real-world contact–that includes a link to an online invoice, where the user can download the invoice.
Instead of downloading the invoice, the victim downloads malware to their device. Ransomware is often spread in this fashion, hoping that the victims will download the invoice in a state of panic, wondering what in the world they are being billed for.
Warning Signs
To keep yourself from being tricked by an invoice impersonation attack, or any other type of phishing email, the best route is to provide training and remain aware of the warning signs.
One of the most common ways a hacker will take advantage of email is by sending a message demanding payment, with a link to make things convenient for the user to do so. The problem with email is that the user is forced to take it on good faith that the message comes from the proper recipient. If it were a phone call, you might recognize that the voice is different from whoever should be calling, and if it were a handwritten message, you might notice a discrepancy–but with a message with no identity, it gets considerably more difficult to identify a falsified message.
If you ever receive an email claiming to be from someone who needs a payment from you, there’s a good chance that the link leading to a “payment portal” is just a link to a ransomware program or other type of threat.
Securing Your Business
Phishing attacks naturally rely on the victim trusting the impersonation, so you can take advantage of this opportunity to sow the seeds of distrust–that is, to train your employees to identify emails and distrust anything suspicious that they receive in their inboxes. Your employees should always be wary of risk factors, but they should also attend regular training sessions that test how much they remember about cybersecurity best practices.
You can also take it one step further by implementing spam filters, malware blockers, and other security solutions designed to prevent infections in the first place. If you minimize the chances that your employees are exposed to threats in the first place, they are less likely to make a mistake that has great ramifications for your network security.
Catalyst Technology Group can equip your business with enterprise-level security solutions designed to augment and maintain network security for small businesses. To learn more about how you can manage the risk associated with security threats, reach out to us at (317) 705-0333.
Tip of the Week: Protecting Your Mobile Device in 2 Easy Steps

Mobile devices are one of the greatest tools available for business use today. However, because society has come to rely so much on mobile devices, these devices have become a treasure trove for cybercriminals to obtain information from. For this week’s tip, we’ll go over some simple ways to protect yourself from such threats.
Do You Really Need to Connect?
Wi-Fi and Bluetooth connectivity give our phones a heightened level of utility, but this benefit can also come with severe risks. Mobile devices, for the sake of simplicity and convenience, are ready and willing to connect with any Wi-Fi or Bluetooth signal they can. Unfortunately, this puts them at risk of being hijacked by any threat that may be lurking on the signal.
To mitigate this risk, make sure that you aren’t connecting to Wi-Fi or Bluetooth signals that aren’t secure and trustworthy. In fact, when not using them, keep these connections disabled just in case.
The same goes for public charging stations. These can also be used to spread threats, so it is better to rely on a portable charger or a wall outlet to power your device.
Furthermore, if you are connecting to something, make sure you aren’t sharing more than you need. For instance, if you need to rent a car while on a business trip, there’s nothing wrong with using Bluetooth to make hands-free calls. However, if prompted, there is no reason to sync your contacts with the car’s storage, effectively handing them to the next person that rents that car. Being cautious as you connect will only help you to stay safe in the long run.
Keep it Locked Up
The contents of your phone shouldn’t be available to just anyone who picks it up. Whether you have access to sensitive business information through the device, or you have apps that help you manage the rest of your life, your information is at risk unless you have protections in place to keep it safe.
The simplest way to do so is to leverage the phone’s built-in security features. Whether your phone accepts PIN numbers, passcodes, or a pattern set it up so that only you know how to open it. Furthermore, with more devices today leveraging biometric and facial recognition technology, there are other means for you to secure your mobile device.
Security is a crucial consideration to keep in mind, whenever you’re using a mobile device. For more information on how you can keep your business resources safe from threats in and out of the office, reach out to Catalyst Technology Group at (317) 705-0333.
Tip of the Week: Google Chrome Extensions for Google Drive

Google Drive lets its users take advantage of a lot of great tools and utilities, and this is only augmented by Google Chrome’s extensions. With these tools at your disposal, you can optimize the way your company takes advantage of Google Drive. Here are some of the best extensions out there that let you utilize Google Drive’s best assets to your advantage.
Drive and Docs Companion
Two extensions called Drive Companion and Docs Companion are great ways to get more out of your Google Drive. They take the two web applications and transform them into virtual desktop applications. Basically, these web apps are turned into applications like any other type of software on your computer. You can open your files through the Drive Companion window, and by doing so, you open up another desktop application window.
Docs Companion is created by the same developer as Drive Companion, the only difference is that it’s specific to Google Docs. Rather than opening up a virtual desktop application of your Google Drive, Docs Companion opens a word processing page for Google Docs.
Click here to download Drive Companion. Click here to download Docs Companion.
Office Editing for Docs, Sheets, and Slides
Google’s productivity suite, which includes Docs, Sheets, and Slides, might be a great solution, but there are users that see Microsoft’s Office suite as a more attractive option. For example, Microsoft Word’s spell checking abilities are much more proficient than Google Docs’. This being said, Google offers superior collaborative abilities. For the best of both worlds, you can use Office Editing for Docs, Sheets, and Slides to use Microsoft products to your company’s advantage.
Office Editing for Docs, Sheets, and Slides allows a user to use these Google apps to access and edit Microsoft Word, Excel, or Powerpoint files, along with the collaborative capabilities that Google provides. All you have to do is drag the Microsoft Word, Excel, or PowerPoint file from your internal drive to a Chrome window, and the proper Google application will load.
In addition, if you’ve shared any of your Microsoft Office files through Gmail, as a web link, or just saved it into your Google Drive, this extension can work in these cases as well.
Click here to download Office Editing for Docs, Sheets, and Slides.
Quick Drive
There is no denying that, as helpful as Google Drive is, it can be a pain to have to navigate it to pull up a specific file. Not only does it take up valuable time, it means that you may have to show off your Drive contents to your clients as you dig up documentation.
As an alternative, Quick Drive gives you a search bar that appears upon clicking the icon in the Chrome Toolbar. Once the name of the document or some keywords are entered, matching documents from your Drive will pop up as options.
To further simplify the process, you can also use the Favorite and Recent tabs in Quick Drive to pull up documents that have been starred or opened recently.
Click here to download Quick Drive.
DriveCast
Another pain that you may encounter when working with Google Drive comes when it is time to present your work to a group and a display or projector is involved. It isn’t always easy to both hook your device up to the appropriate display, at least without making it more difficult to present the information or blocking your audience’s view. However, this extension makes presenting the contents of your Drive much easier, provided that you have access to a Google Chromecast. With DriveCast, any content in a supported format can be cast from your Drive directly to a Chromecast device.
Once DriveCast is installed and your computer has connected to the appropriate Chromecast, DriveCast will open a new tab in your browser that lists all of your Google Drive folders alphabetically. Once you’ve found the content you want to cast, select the file and click ‘DriveCast’ in the window that appears beneath the address box.
Click here to download DriveCast.
It is our hope that these extensions will make your day-to-day operations that much easier. Are there any extensions that you’ve found particularly helpful? Tell us about them in the comments!
Tip of the Week: Your Productivity Doesn’t Depend on the Internet

It is an expectation for the modern business to rely on the Internet in order to complete its daily function. As a result, anytime there is an Internet outage, many employees may find themselves lacking purpose or direction. However, a lack of Internet doesn’t have to mean a lack of productivity. For this week’s tip, we’ll review some ways your staff can be productive without an Internet connection.
Keeping Things Organized
Office clutter happens. It is the natural side effect of a team being focused on getting task after task completed. If the files on your local network need some reorganization, or the workspace itself needs a little TLC, an Internet outage provides an ideal time to tidy things up a bit.
A tidy workspace will benefit the organization as a whole, as well as each employee. After all, the fewer distractions that an employee has on their desk, the easier it is for them to stay focused (and the easier it is for someone else to find a resource should that employee be away from the office that day).
Furthermore, it is much easier for one to find things in an organized closet or cabinet than one that has everything thrown in and piled up without any rhyme or reason, which translates to saved time. Using the time that the Internet is down to go through your storage and organize it will allow you to achieve an important task without sacrificing another.
If you can still access your internal network’s data storage, an Internet outage also presents the opportunity to reorganize this storage space as well. Using folders to organize the files on your desktop into a logical system of categorization will also help you to find them later when they can be used to achieve something.
Team Building
While technology has enabled businesses and their employees to experience greater connectivity than ever before, this has also contributed to the seemingly opposite effect of creating some barriers between team members as well. After all, it is much harder to build the interpersonal relationship that develops into the synergism that you want and expect from your team when most of their communication takes place through a screen. Additionally, this synergism will often have a positive benefit when collaboration is part of your team’s responsibilities. Therefore, it only makes sense to encourage the development of these interpersonal relationships when the Internet doesn’t allow for typical workplace duties to be completed.
As they wait for their Internet access to come back, your team can hold meetings that don’t need the Internet in order to be run. These meetings could even be relatively simple brainstorming sessions where new ideas can be shared freely. Alternatively, you might encourage your teams to reach out to departments they don’t often do business with in order to get to know the other people who work alongside them.
This can benefit management as much as it benefits the workforce. If you and the rest of your management team reach out to employees with the intent of getting to know each other better, you can better shape your management style. By doing so, you encourage your employees to be more engaged and communicative, and you can personalize your approach to each employee for the highest impact.
Mobile Devices
While there are times that an improperly used mobile device can be a detriment to office focus and productivity, there are also times that these devices, leveraged properly, can be your best bet if you want productivity to be preserved. Mobile devices provide the chance that, if your business’ Internet should fail, your employees could continue their work. With the right proactive planning, your workforce could continue their tasks through the use of their own mobile data, with reimbursement dictated by a Bring Your Own Device strategy, or on a device that your company provides. If you’d like help in developing any of these measures, Catalyst Technology Group can provide that assistance.
In the meantime, what do you do to help stay productive when the Internet fails? Share some of your ideas with us in the comments!
Tip of the Week: Never Pay to Print Business Cards Again

It’s just good business to hand out your business card to prospective clients, and it has been for a very long time. As far back as the Renaissance, special guests were announced with name cards that displayed who the guest was and what types of greetings were due. It wasn’t until the Industrial Revolution that business cards became primarily a means of displaying trades or professional skills. Business cards are mostly used for marketing and networking in the modern age, and your organization should be using them.
Software developers have started to create applications that make using business cards even easier. Here are some of the features of these apps and how you can use them to your advantage.
Drop
Drop is an app that serves two major purposes. It’s basically a virtual business card, but it also lets you take a quick snapshot of any new business card you’re given and save it automatically into a contact. Now you won’t have to worry about keeping the card safe and sound in your wallet.
It’s easy to see why Drop is such a great networking tool. Since you aren’t reliant on keeping the card on your person, you will have an easier time keeping track of it in your smartphone. However, you have to watch out for the app misreading the names or looking at the wrong address.
Overall, Drop is a solid solution, and it’s compatible with both Android and iOS devices. It even has a geolocation feature that can group your cards together based on the scanning location, or extract information from a business card you had already taken a photo of. Finally, you can create your own digital business cards, which is something that you could do even without having the app installed.
CamCard
CamCard is a solution that helps your business manage its business cards, as well as scan and collect information associated with them through a mobile app. Since it’s a cloud-based service, your scanned cards can be accessed on any connected device, be it a tablet, smartphone, or your web browser. You can also annotate scanned cards for any meetings or scheduled appointments that might be associated with them.
CamCard also has a business app that you can use to share business card information with your organization’s internal sales department. You can use this app to keep your organization up-to-date on information sharing. Information can be shared to either your entire organization or by department. Furthermore, integration with Google Contacts, Outlook Contacts, and Microsoft Excel can be achieved, and you can set up user access roles based on who you want to access this vital information.
How do you manage your business cards? Let us know in the comments.
Tip of the Week: Don’t Let Your Old Android Device go to Waste

Unless you’re the trade-in or hand-me-down kind of person, it’s likely that you have a supply of old Android devices squirrelled away somewhere. You know, just in case the one who have now breaks. However, these old devices can be useful in other ways around the office. For this week’s tip, we’ll go over three alternate uses for your mobile device in the office.
Portable Trackpad
There are assorted applications available that allow you to link your old phone to your computer and use it as an alternative controller to your mouse. These apps often offer specialized features that give you better control over media playback and other useful workplace utilities.
Just be sure to install whatever app you select from the Google Play store, as it is the safest option out there for downloading apps. However, you should also make sure that your IT department signs off on you adding these apps to devices used for work.
Universal Remote
If you happen to use smart devices in your office, your old phone could become a central control hub for them. Download the necessary apps from the Google Play store, and in no time, you’ll be able to control any of the gadgets you have installed around your office with a dedicated remote, eliminating the need for the bulky included remotes that accompany many of these devices, as well as the need to take up space on your current mobile phone.
Security Camera
Similarly to using your old device as a universal remote, you can find apps on Google Play that can turn it into a security camera with a few different features. By doing so, you can boost your office’s security with the option to check in on goings-on via a web browser, record the footage, and even have the camera activate when motion is detected.
Bonus Purpose: Donate the Phone to BOINC
The Berkeley Open Infrastructure for Network Computing, or BOINC, allows you to donate the computing resources of your old phone to assist research teams in their efforts towards scientific breakthroughs. So far, resources dedicated to BOINC have powered research into the climate, molecular dynamics, genetic sequencing, measured the efficacy of malaria treatments and the power of earthquakes, as well as many other scientific causes.
To participate, all you have to do is download the BOINC app from the Google Play Store and select what research you want to commit your phone’s resources to. The app will only run if your device is both charged and plugged in, as so not to leave you with a drained phone, and can be set to only transmit data over Wi-Fi, saving your data.
What other uses have you come up with for your old Android devices? Let us know in the comments, and make sure to subscribe to our blog!
Tip of the Week: Why You Should Reconsider Your Best Practices

The term “best practice” has been used by businesses for years to describe the optimal way of performing a particular task. However, before fully adopting them into business operations, it is important for these practices to be examined and deemed to be beneficial to an individual company’s circumstances. If they are not, a company risks much by adopting a misplaced best practice.
The major problem is that “best practices,” while useful if applied properly, is a term that has largely become a buzzword for businesses to use in their communications. This is dangerous, as there is a lot put at stake based on the term “best practice” alone. Therefore, it is crucial that so-called best practices are reviewed and examined before a business puts strategies based on these practices into place.
This was the argument made by Professor Freek Vermeulen in his recent book, Breaking Bad Habits: Defy Industry Norms and Reinvigorate Your Business. An interview with the Harvard Business Review allowed him to discuss the phenomenon further.
To provide an example of how best practices may not always be of a business’ best interest to follow, Vermeulen discussed a South African bank called Capitec and how they relied on reverse benchmarking to identify how to become an outlier in their industry.
The practice of reverse benchmarking can be summed up as the process of examining how one’s industry typically operates in order to identity weak spots in accepted practices and improve internal business operations. This can often lead to the abandonment of what is considered the status quo, if not heavily modifying it.
Capitec’s examinations revealed that other banks in South Africa had a tendency to close at four o’clock in the afternoon. To abandon this status quo, industry-standard practice, Capitec not only extended their hours to enable those who worked during the day to see to their banking needs once their work day was over, they even implemented Saturday hours in many of their branches. As a result, Capitec has since carved out a healthy market share for themselves.
This account is just one example that shows how what is standard practice might not be what is best for the business following it. However, many businesses give some push back when directly asked why they follow the practices they follow. These businesses often will respond with some statement that essentially says “this is what is comfortable” or “this is how it has always been done.” These answers are a good sign that, according to Vermeulen, an organization needs to run a self-audit to determine if they are enacting practices because they benefit the organization, or if they are simply resisting change.
Furthermore, there is the risk inherent in assuming that something that made a business successful is automatically a best practice. As Vermeulen mentioned in his interview, many companies who have reached the top may have simply been lucky as they enacted risk-laden strategies, and most of the companies who tried similar strategies have long since failed and been forgotten.
Of course, changing established practices and patterns is not easy for businesses to do. Vermeulen notes this, stating that many companies will hold out until they have no choice but to make a change. This is usually done at the point where their profits and productivity take a hit. However, waiting until this point often makes change more difficult for these companies. According to Vermeulen, the key to avoiding unnecessary difficulty is simple: “Be proactive.”
By taking the opportunity to audit your business practices before your company is stuck in a life or death situation, you can more clearly see where your company is weakest. Better yet, you will be able to remedy these weaknesses before your company is at risk.
Catalyst Technology Group can help you evaluate your IT solutions to ensure that they are not contributing to any weaknesses that your company may suffer from. Call us at (317) 705-0333 for more information.
Tip of the Week: Cortana Can Do Even More than You Might Realize
One of the most recognizable names in technology isn’t a person, it’s a virtual assistant: Cortana. While Cortana has been of great use to many users, sometimes that user isn’t actually the person who owns the device and is just someone else in the same room. This can be annoying, but there’s a way to acquaint Cortana with a single user’s voice and listen to them exclusively.
To set this up, you’ll need to access Cortana’s Settings. First, click on the Cortana Icon that appears on the taskbar.

Next, access the settings menu for Cortana by clicking on the gear icon in the Cortana window that appears.
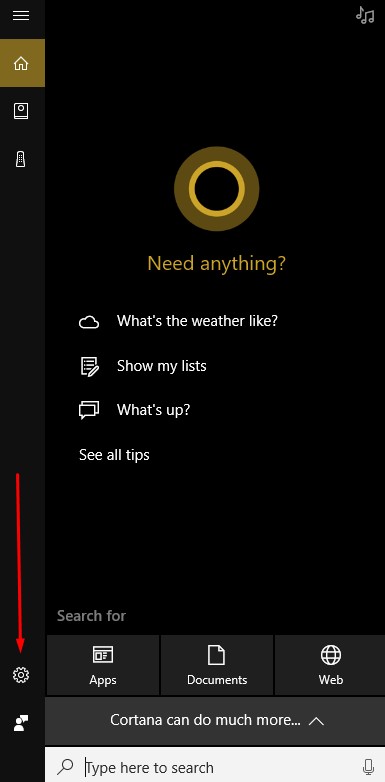
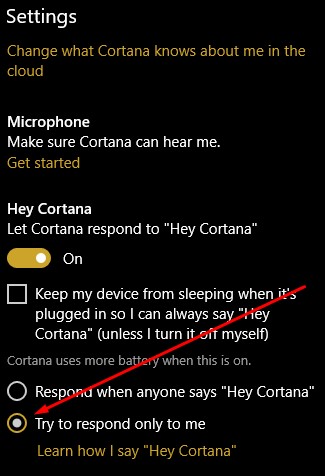
Activate Let Cortana respond to “Hey Cortana” and select Learn how I say “Hey Cortana.”
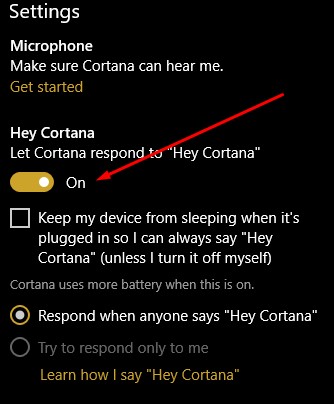
Once you do so, you will be prompted to recite six phrases so that Cortana can establish how you will say “Hey Cortana.”
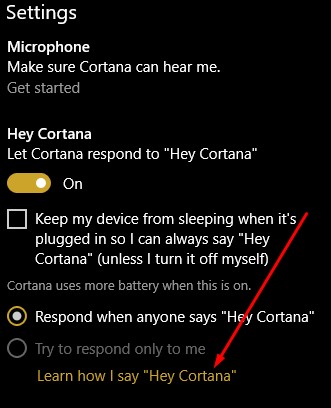
After this exercise is completed, go back to Cortana’s settings and confirm that try to respond only to me is selected.
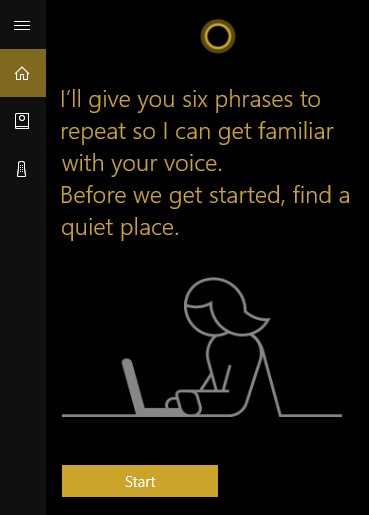
Cortana is now primed to listen to only you and you can now use it for many purposes, including to navigate Windows 10.
Are there any other assistants you use, like Alexa, the Google Assistant, Siri, or Bixby? Which one is your favorite? Tell us why in the comments section!

